Passwords have been with us for ages. In early 60s, at MIT, researchers started to explore possible ways to enable computer systems to tell the difference between users who were using the systems, or to find a way to identify, or verify that the users are who they say they are, that is – to authenticate users. In 1961 an MIT employee printed a list of passwords and distributed it to other users – it was a first known breach.
Since then, users and administrators have been struggling with passwords and have been trying to make systems more secure. We, both users and administrators, are not fans of passwords because they are not perfect and we have few problems with passwords, here and there.
Generally, passwords are not easy to use, difficult to remember – especially good and complex passwords are difficult to remember. On the other hand, easy to remember passwords are not so hard to guess. Add to password complexity a non-traditional keyboard, frequent password changes, passwords that are reused across multiple locations and devices and you have a recipe for a forgotten or stolen passwords, breached systems or frequent password change calls to support personnel. Not only calls cost substantial amount of money but everything related to a password loss or a breach incur money loss as well.
Technically, password attacks are not too complex: the attackers have only a single factor of authentication to deal with. Username and password combination counts only as a single factor authentication: username identifies the user trying to access a system and a password is used as a single form of authentication.
As much as we, users and administrators hate passwords and have problems with them, hackers and attackers love the passwords for all their faults and shortcomings.
Fortunately, passwords are becoming a thing of the past. Since passwords make our systems more vulnerable, forcing constant password changes and making passwords more complex does not help in raising the security of username and password combination. We needed better protection and we added a second factor of authentication which made the username and password combination more secure – the Multi Factor Authentication was born. Along with a password, we suddenly had to supply additional information to log in: time-bound one-time password or in some cases pre-approved list of codes or phrases. Unfortunately having multi factor authentication still is not enough to keep up with increasingly high number of cybersecurity threats. More than 80% of hacking related breaches use either stolen or weak passwords according to a Verizon 2017 Data Breach Investigations Report.
But then, even if we use multifactor authentication, which is inherently more secure, we still use passwords, which is the insecure or inconvenient part in this story. What if we replace a password with a verification factor, preferably with two or more verification factors, and store them somewhere, for example on a device, such as a computer or on a physical key. That way the credentials would never leave the device and we would be protected from phishing, password loss, over-the-shoulder-snooping or credential theft.
The benefits of using Passwordless authentication are numerous: there are still passwords out there, in the background, but we do not need to remember, store, change and enter passwords anymore.
At Microsoft Ignite 2017, Microsoft shared its vision and four-step approach to a Passwordless world, how to detach ourselves from passwords and steps to achieve password freedom.
- Develop a password replacement offering. We need something to replace passwords, and that ‘something’ preferably needs to be more secure than the current offering. Fast forward to 2021 and we are witnessing improvements in this area, and variety of products and possibilities to choose from. Having more choices is good but I guess some options will become more prevalent in the future as private and business consumers figure out what works best for them.
- Reduce user-visible password surface area. This step requires a strategy to reduce using passwords to a minimum, or to reduce passwords’ “surface”. The ideal situation would be where users know their passwords, but they never need to use them, they are never prompted to use them or type them anywhere. This significantly reduces password leaks and phishing attempts unsuccessful.
- Transition into a Passwordless deployment. This stage includes transitioning to a Passwordless world where users:
- Never change their passwords
- Never type their passwords
- Do not know their passwords.
As an example, a user logs in to Windows 10 using Windows Hello for Business and uses single sign-on to access Azure and Active Directory resources.
- Eliminate passwords from the identity directory. The final stage of a truly Passwordless world is an environment where passwords merely do not exist.
How to go Passwordless with Microsoft? Here are some password replacement options you might consider: Windows Hello and Windows Hello for Business, Microsoft Authenticator App, or a FIDO2-compliant security key. Windows Hello and Windows Hello for Business provide excellent user login experience – it supports biometric authentication using your fingerprint or face, along with a screen gesture or PIN to login.
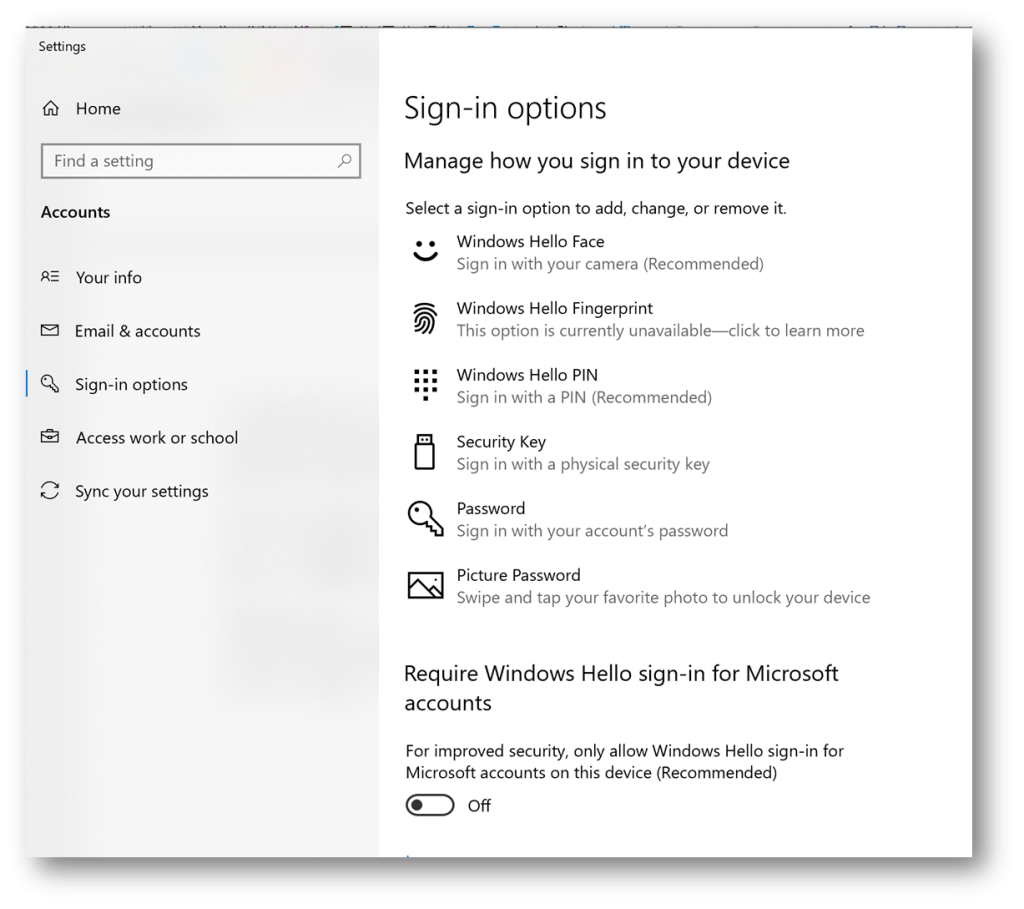
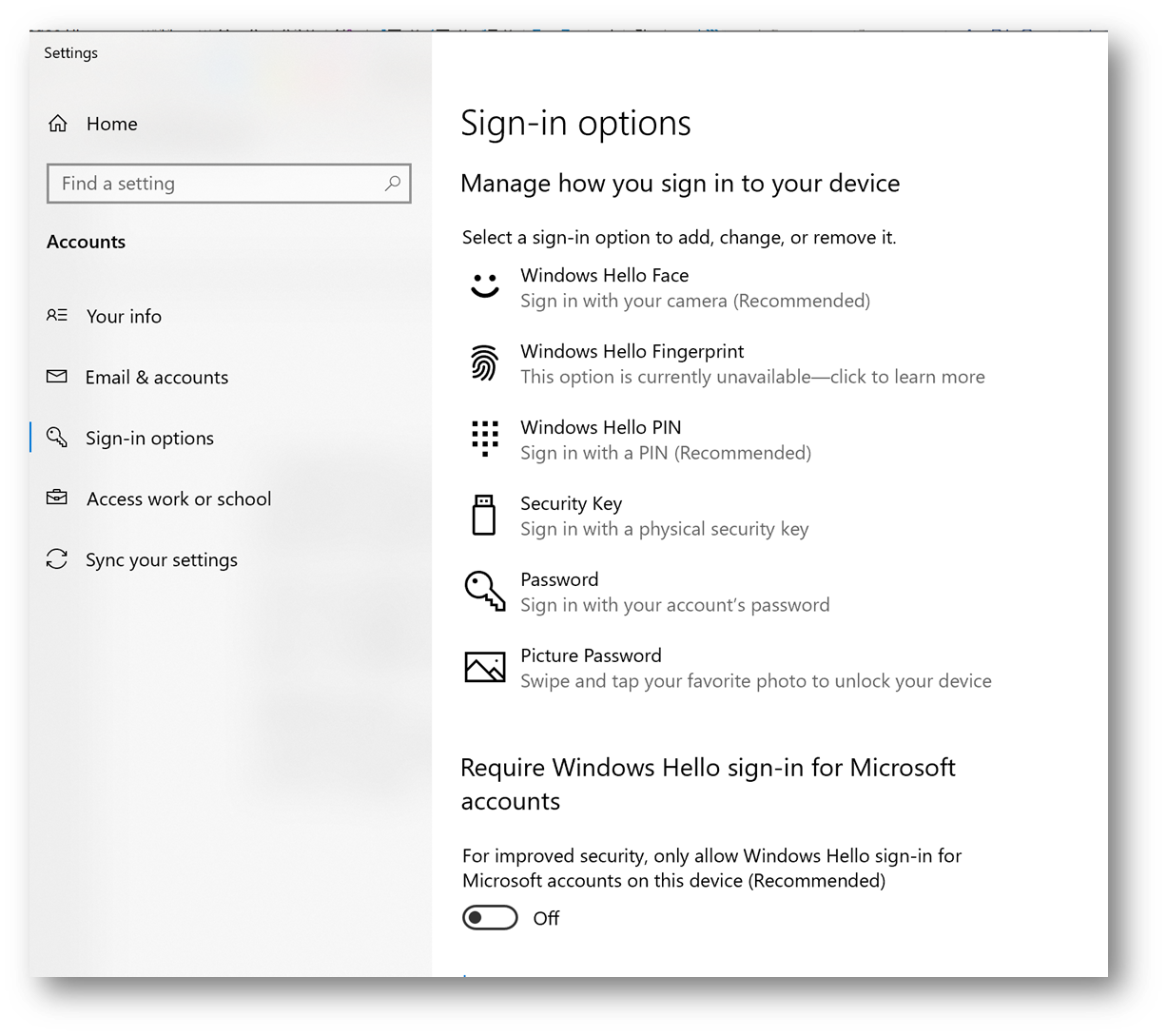
In windows 10, visit Settings and Sign-In options to manage sign-in options for your device. There are lot of options to choose – from Windows Hello Face (you will need IR-capable camera), Windows Hello Fingerprint (enabled if you have a compatible fingerprint reader) and Windows Hello PIN, to the possibility to set up sign-in with a physical security key.
In contrast to Windows Hello, Windows Hello for Business is configured via Group Policy or Mobile Device Management (MDM) policy and uses certificate-based or key-based authentication. In both cases, biometric or PIN information is unique to a device where it has been set up and never leaves the device. During the provisioning of Windows Hello, cryptographic key pair is bound to the Trusted Platform Module (TPM) chip if a device has one, or in software. Using passwords is less secure as passwords are shared secrets between a user and a server and transmitted over the network, susceptible to interception.
Microsoft Authenticator App provides greatest convenience, flexibility, and cost for experiencing Passwordless authentication, for both personal and business scenarios. It supports biometrics, push notifications, time-bound one-time passcodes (TOTP or OTP codes). Not only this, but it supports cloud backup and restore, importing passwords from Google Chrome and other apps and can fill saved passwords on sites and apps. Additionally, passwords saved in Microsoft Edge will synchronise with Microsoft Authenticator App for seamless mobile experience. It is free to download from the Apple Store and Android app stores and you can use it with almost every account: Google, Amazon, GitHub, Twitter, Facebook, LinkedIn, Instagram, and gazillions of others.
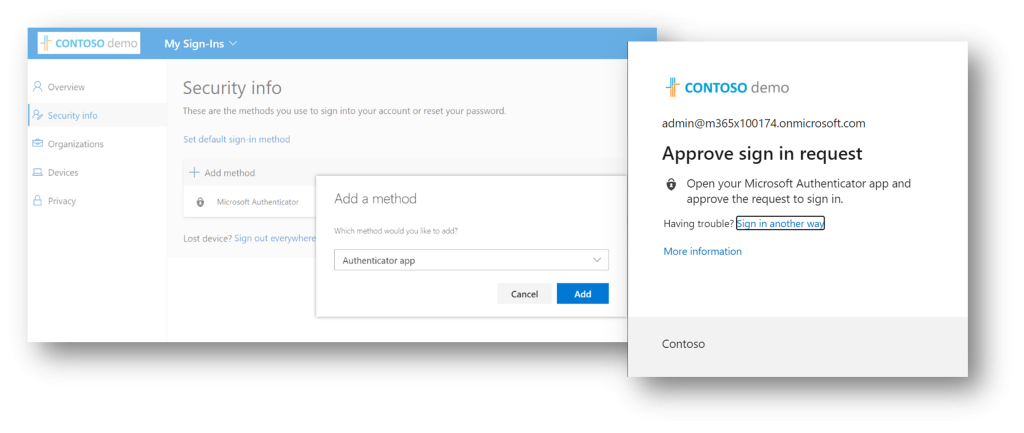
In Azure Active Directory, setting up Microsoft Authenticator App as a sign-in method and a second factor of authentication is easy, it takes no more than two minutes and it bring numerous benefits. Once set up, sign-in experience removes entering a password and you are required to open Microsoft Authenticator app to approve the request to sign in by entering a code or confirming on screen.
Passwordless authentication offers additional benefits beyond being merely a second multi-factor authentication method – more secure sign-in without having to enter a password.
You can use Microsoft Authenticator App as a Passwordless sign-in option if it has been enabled in Azure Active Directory. Instead of entering a password, users get a push notification to verify legitimacy of a sign-in event by matching a number and providing a PIN, fingerprint, or a face scan to complete authentication process.
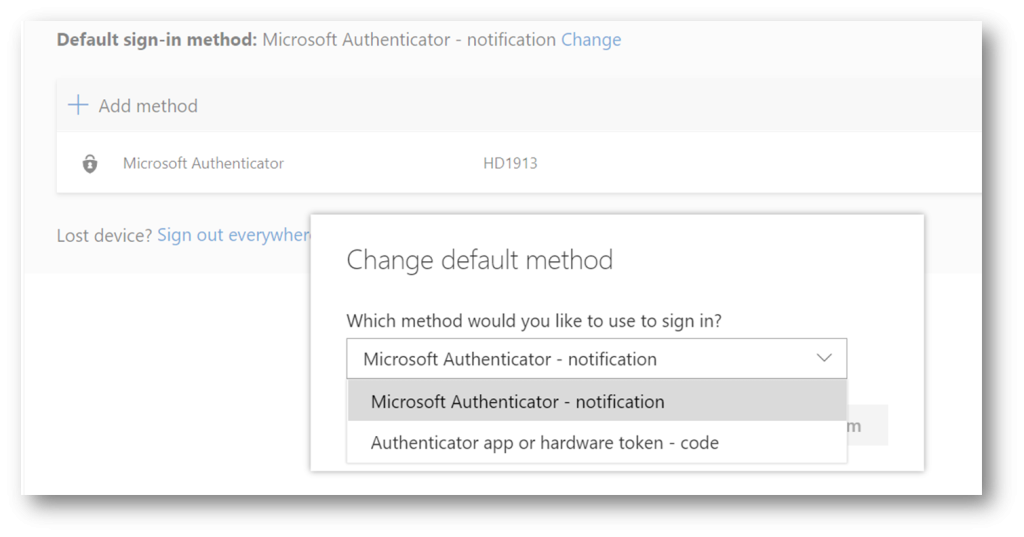
Recently, two Passwordless authentication options completed their preview stage and reached general availability – FIDO2 Security Key (1) and Microsoft Authenticator (2). Two more options are still in a preview phase, Text Message and Temporary Access Pass (3).
To enable Microsoft Authenticator App as a Passwordless option, open Azure portal, go to Azure Active Directory and chose Security. Click on a Microsoft Authenticator entry and Enable (4) use for All Users or Selected Users. Optionally, configure Authentication mode (5) and choose Passwordless, Push or Any mode (6).
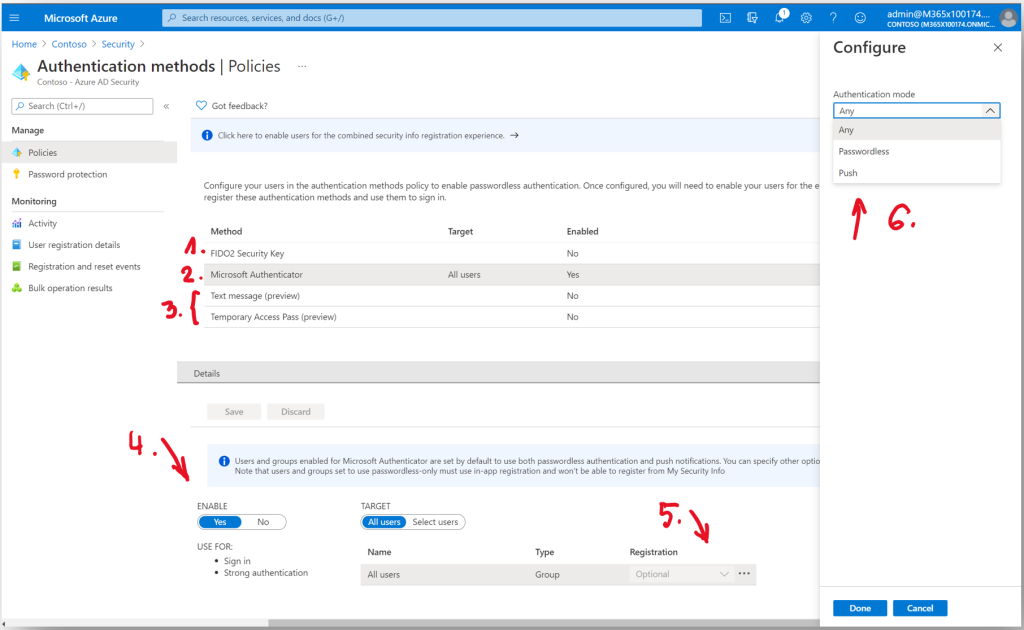
FIDO2 Security Key is a second Passwordless authentication method that brings several benefits. It offers improved usability as using hardware-based security key is easy and fast, and strong account security as it replaces passwords with strong hardware-based authentication using private/public key cryptography. Moreover, a single security key can work across numerous accounts with no shared secrets.
FIDO2 stands for Fast IDentity Online and it is the Passwordless evolution of FIDO U2F. FIDO2 cosists of two components, a web API (WebAuthn) and a Client to Authenticator Protocol (CTAP), both responsible for a passwordless sign-in experience. Older FIDO U2F protocol was renamed to CTAP1 in the WebAuthn specification, and it was used to work with external authenticators.
FIDO2 security keys usually use USB form factor but could also use NFC or Bluetooth (or BLE – Bluetooth Low Energy)
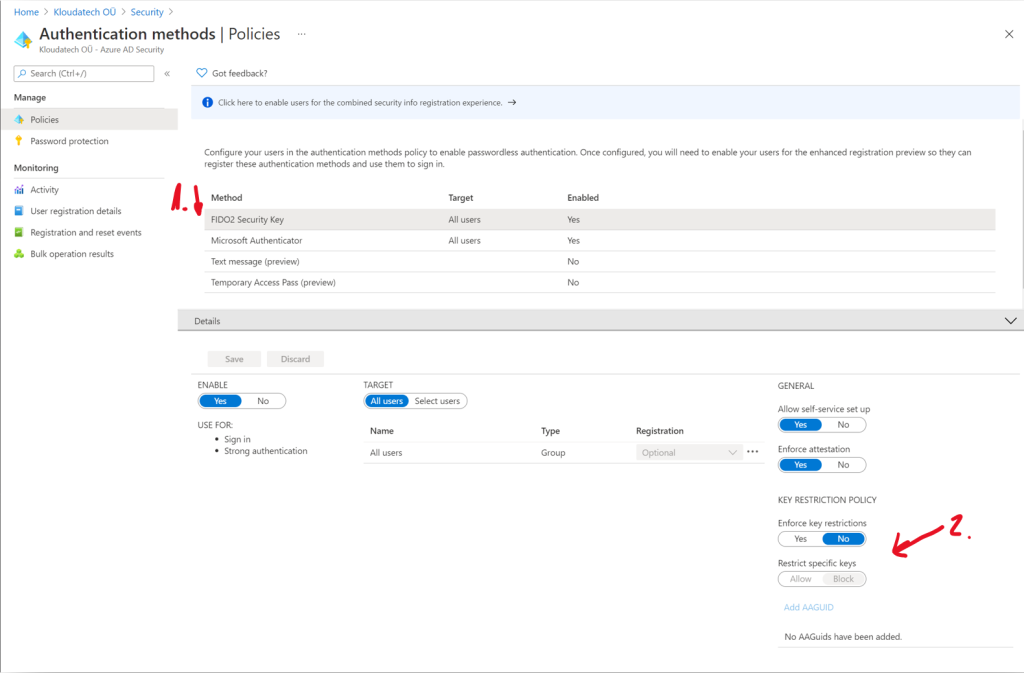
The process of setting up a FIDO2 Security Key (1) as a Passwordless option in Azure Active Directory is like setting up Microsoft Authenticator App. Businesses will welcome a key restriction policy option to restrict specific keys (2) to either Allow or Block usage of certain keys. The FIDO2 specification mandates that an Authenticator Attestation GUID (AAGUID) must be provided during attestation. An AAGUID is a 128-bit identifier indicating the type of the authenticator. Authenticators with the same capabilities and firmware can share the same AAGUID. This is how the Passwordless sign-in experience using a security key looks like:
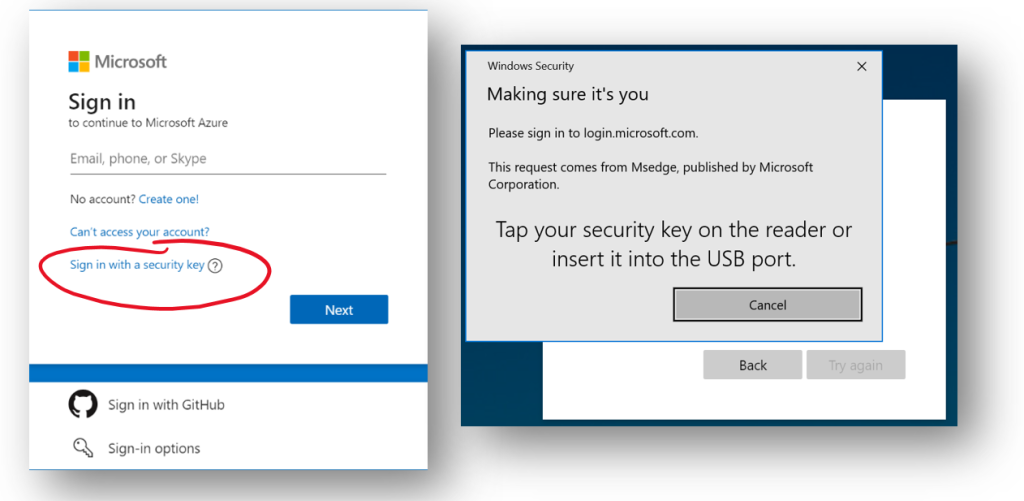
On a sign-in screen, choose Sign in with a security key, insert a security key if you have not already done so, touch a security key and that is it! Fast, simple and what is most important – secure. The journey is a long one, but the industry is moving in the right direction, and I cannot wait to enjoy Passwordless future, where passwords no longer exist.